The First Maker Space and Tech Community For Markham, Richmond Hill, Thornhill, & Vaughan.
3D Printing, Amateur Radio, Laser Cutting, Electronics/Arduino, Programming/A.I., and more!

About YLab
We are York Region’s first maker space. We’re all volunteer, non-profit and member supported, with a wide variety of interests. We’ve been operating our maker space in the basement of the historic David Dunlap Observatory administration building in Richmond Hill.
Upcoming Events: Even though we are closed for COVID, we have a slate of on-line events scheduled – many for non-members too! Check out all the events here.
Upcoming Events: Even though we are closed for COVID, we have a slate of on-line events scheduled – many for non-members too! Check out all the events here.
What We’ve Been Up To.
The best way to keep up to date with us is to follow our blog. It’s regularly updated with our activities and shenanigans. Below is all our announcements.
The Fine Print
A brief summary of some of the information you’ll probably want to know if you’re interested in joining our space. For more details, visit the about us page.
More About What We Do
We host tech talks, classes and seminars at the DDO and in other location. Most importantly, we work on projects and help each other. It gets better every week.
We welcome anyone who interested in software, Arduino, 3D Printing, laser cutting, robot making and toy hacking, amateur radio and whatever else we can think of.
We welcome anyone who interested in software, Arduino, 3D Printing, laser cutting, robot making and toy hacking, amateur radio and whatever else we can think of.
Our Equipment
Please note that our equipment is YLab owned or lended to us by members, so we regularly add new gear.
-
Laser Cutter with a 24″ x 36″ bed
-
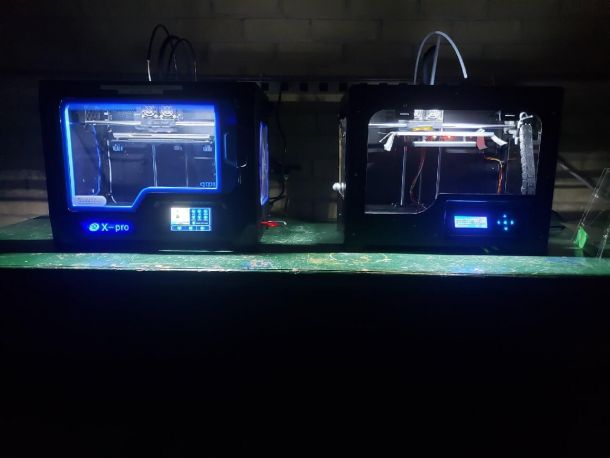
3D Printers (PLA and ABS filaments)
-
Oscilloscopes
-
Soldering Tools
-
Amateur Radio Gear
-
& More!
Membership
Currently accepting applications. Note that we have several levels of membership, and their details are listed below. Click here for more information.
Additionally, as membership increases, 100% of the funds go back into the space. We’re a purely volunteer based and not-profit organization.
Additionally, as membership increases, 100% of the funds go back into the space. We’re a purely volunteer based and not-profit organization.
Contact Us
We’re always looking for new classes, tutorials, information, or anything else that we think would be fun for our members.

YLab
Located inside the Richmond Hill David Dunlap Observatory
123 Hillsview Dr, Richmond Hill, ON L4C 1T3
123 Hillsview Dr, Richmond Hill, ON L4C 1T3
© YLab Inc. All rights reserved.